Proposed Cryptographic Solutions
Daniel J. Cooke, Andres Guzman, Brooklyn Mesia, Jacob Palmer, Shawn Shields, Milan Zanussi,Kristen Garcia, Lindsey Kim, Dr. Liljana Babinkostova, Dr. Marion Scheepers, Jay Radcliffe, and Robert Erbes
Introduction
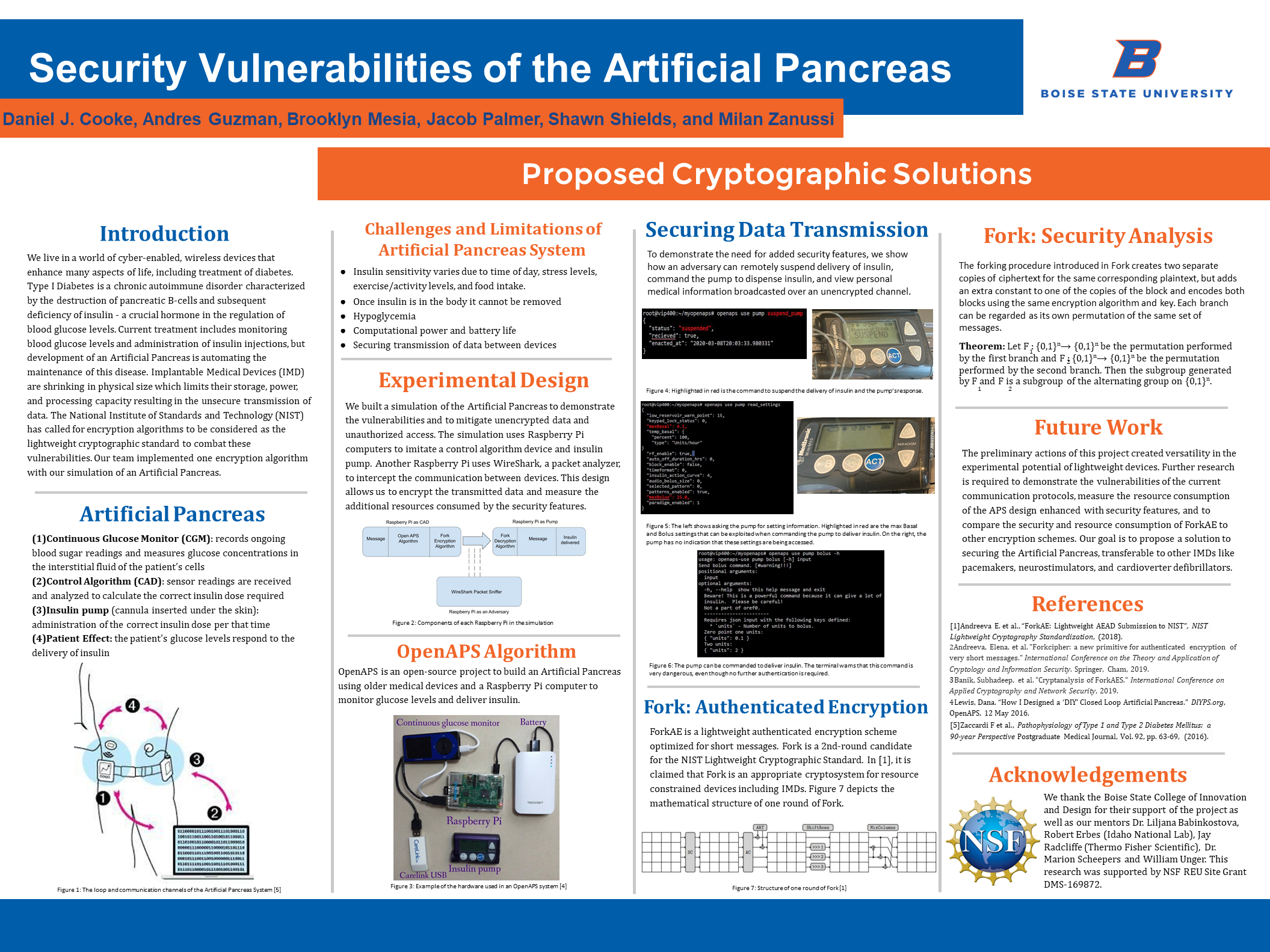
We live in a world of cyber-enabled, wireless devices that enhance many aspects of life, including treatment of diabetes. Type I Diabetes is a chronic autoimmune disorder characterized by the destruction of pancreatic B-cells and subsequent deficiency of insulin – a crucial hormone in the regulation of blood glucose levels. Current treatment includes monitoring blood glucose levels and administration of insulin injections, but development of an Artificial Pancreas is automating the maintenance of this disease. Implantable Medical Devices (IMD) are shrinking in physical size which limits their storage, power, and processing capacity resulting in the unsecure transmission of data. The National Institute of Standards and Technology (NIST) has called for encryption algorithms to be considered as the lightweight cryptographic standard to combat these vulnerabilities. Our team implemented one encryption algorithm with our simulation of an Artificial Pancreas.
Artificial Pancreas
- Continuous Glucose Monitor (CGM): records ongoing blood sugar readings and measures glucose concentrations in the interstitial fluid of the patient’s cells
- Control Algorithm (CAD): sensor readings are received and analyzed to calculate the correct insulin dose required
- Insulin pump (cannula inserted under the skin): administration of the correct insulin dose per that time
- Patient Effect: the patient’s glucose levels respond to the delivery of insulin
Challenges and Limitations of Artificial Pancreas System
- Insulin sensitivity varies due to time of day, stress levels, exercise/activity levels, and food intake.
- Once insulin is in the body it cannot be removed
- Hypoglycemia
- Computational power and battery life
- Securing transmission of data between devices
Experimental Design
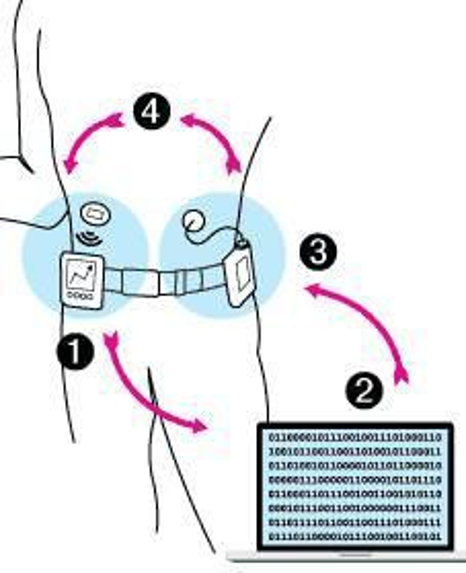
We built a simulation of the Artificial Pancreas to demonstrate the vulnerabilities and to mitigate unencrypted data and unauthorized access. The simulation uses Raspberry Pi computers to imitate a control algorithm device and insulin pump. Another Raspberry Pi uses WireShark, a packet analyzer, to intercept the communication between devices. This design allows us to encrypt the transmitted data and measure the additional resources consumed by the security features.
OpenAPS Algorithm
OpenAPS is an open-source project to build an Artificial Pancreas using older medical devices and a Raspberry Pi computer to monitor glucose levels and deliver insulin.

Securing Data Transmission
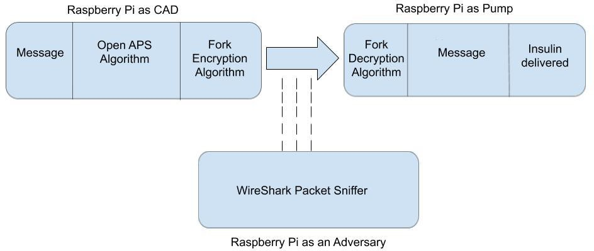
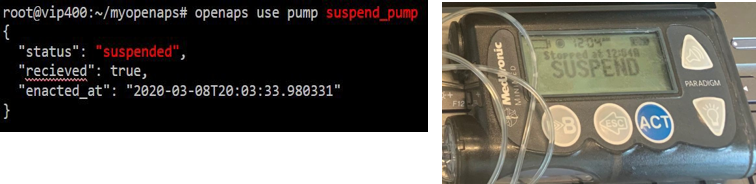
To demonstrate the need for added security features, we show how an adversary can remotely suspend delivery of insulin, command the pump to dispense insulin, and view personal medical information broadcasted over an unencrypted channel.

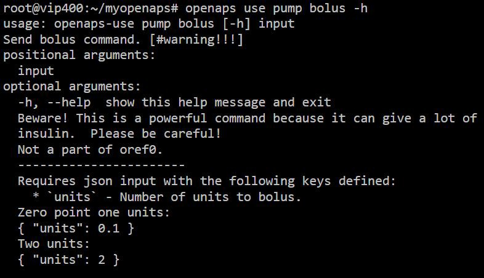
Fork: Authenticated Encryption
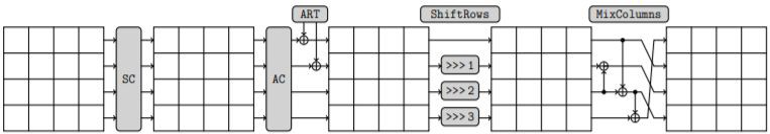
ForkAE is a lightweight authenticated encryption scheme optimized for short messages. Fork is a 2nd-round candidate for the NIST Lightweight Cryptographic Standard. In [1], it is claimed that Fork is an appropriate cryptosystem for resource constrained devices including IMDs. Figure 7 depicts the mathematical structure of one round of Fork.
Fork: Security Analysis
The forking procedure introduced in Fork creates two separate copies of ciphertext for the same corresponding plaintext, but adds an extra constant to one of the copies of the block and encodes both blocks using the same encryption algorithm and key. Each branch can be regarded as its own permutation of the same set of messages.
Theorem
Let F1 : {0,1}n → {0,1}n be the permutation performed by the first branch and F2 : {0,1}n → {0,1}n be the permutation performed by the second branch. Then the subgroup generated by F1 and F2 is a subgroup of the alternating group on {0,1}n .
Future Work
The preliminary actions of this project created versatility in the experimental potential of lightweight devices. Further research is required to demonstrate the vulnerabilities of the current communication protocols, measure the resource consumption of the APS design enhanced with security features, and to compare the security and resource consumption of ForkAE to other encryption schemes. Our goal is to propose a solution to securing the Artificial Pancreas, transferable to other IMDs like pacemakers, neurostimulators, and cardioverter defibrillators.
References
- Andreeva E. et al., “ForkAE: Lightweight AEAD Submission to NIST”, NIST Lightweight Cryptography Standardization, (2018).
- Andreeva, Elena, et al. “Forkcipher: a new primitive for authenticated encryption of very short messages.” International Conference on the Theory and Application of Cryptology and Information Security. Springer, Cham, 2019.
- Banik, Subhadeep, et al. “Cryptanalysis of ForkAES.” International Conference on Applied Cryptography and Network Security, 2019.
- Lewis, Dana. “How I Designed a ‘DIY’ Closed Loop Artificial Pancreas.” DIYPS.org, OpenAPS, 12 May 2016.
- Zaccardi F et al., Pathophysiology of Type 1 and Type 2 Diabetes Mellitus: a 90-year Perspective Postgraduate Medical Journal, Vol. 92, pp. 63-69, (2016).
Acknowledgements
We thank the Boise State College of Innovation and Design for their support of the project as well as our mentors Dr. Liljana Babinkostova, Robert Erbes (Idaho National Lab), Jay Radcliffe (Thermo Fisher Scientific), Dr. Marion Scheepers and William Unger. This research was supported by NSF REU Site Grant DMS-169872.
Additional Information
For questions or comments about this research, contact