Phishing attacks are becoming more sophisticated, and recently, several successful attempts have targeted Boise State University faculty and staff. These scams aim to steal your account credentials, which hackers can then use to alter direct deposit information and compromise personal data.
A concerning number of our colleagues have fallen victim to these attacks. The following are examples of recent phishing emails, along with the signs of what to recognize to avoid compromising your data:
Workplace safety email
An email with the subject, “Workplace Safety: Updates on Recent Health Developments,” successfully deceived several faculty and staff. Many faculty and staff members were misled by this email.
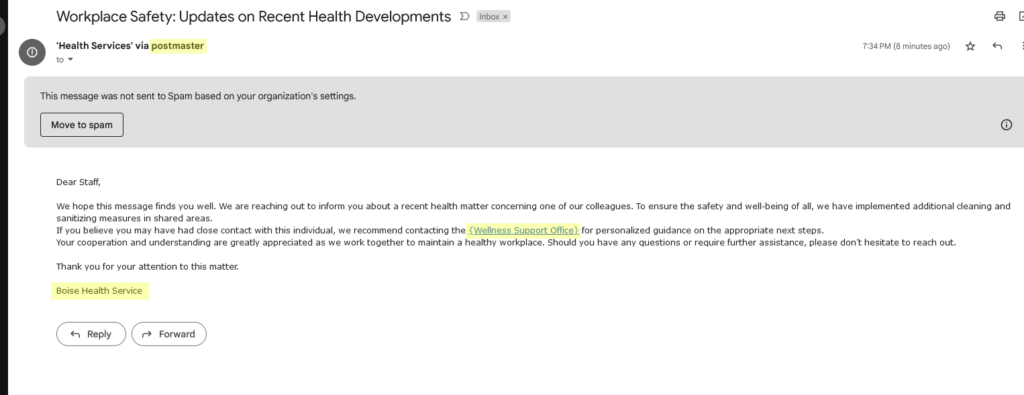
Signs this email was a phishing attempt

Suspicious sender: While Boise State does have a ‘postmaster’ account, it is not used to send targeted or mass email. Instead, it is an administrative email account used for managing and overseeing the function of our email domain.
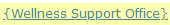
The email recommends contacting the Wellness Support Office: The university does not have a ‘Wellness Support Office’ (it does have a Wellness Services department). The curly braces surrounding the link text are red flag and should prompt caution.

The email is signed from Boise Health Service: The university does not have a ‘Boise Health Service’ department (it does have a Boise State Health Services department).
Fake login page: Clicking on the ‘Wellness Support Office’ link directed users to a fraudulent login page on a compromised external website. Although the page looked like Boise State’s, the web address was unrelated to the university.
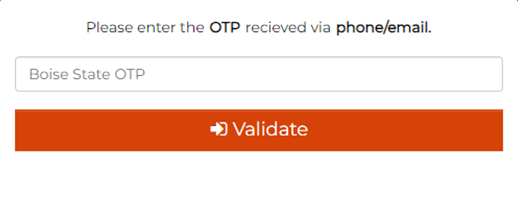
The fake login page requested a Duo security code: After signing in to the fake login page (which gave away the employee’s username and password), the employee encountered a Duo code prompt Boise State does not use.
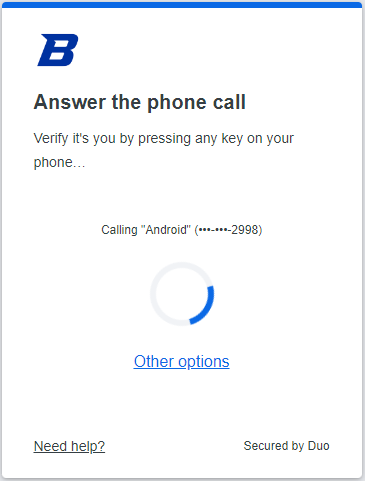
A Duo Prompt for login confirmation: The hackers next logged in using the employees username and password, then sent an Duo Security notification. The employees received the notification and confirmed it. Note that if you receive a Duo authentication method that you don’t typically use (i.e. getting a phone call when you typically use Verified Push) you should not accept the prompt. Additionally, you should always treat Duo prompts that appear when you are not actively logging in as suspicious.
While the fake login page and Duo prompts are clever, they would have been avoided if the victims had recognized the unusual elements of the email message itself and suspected it could be a phishing message.
University Health Services “Infection Reported” email
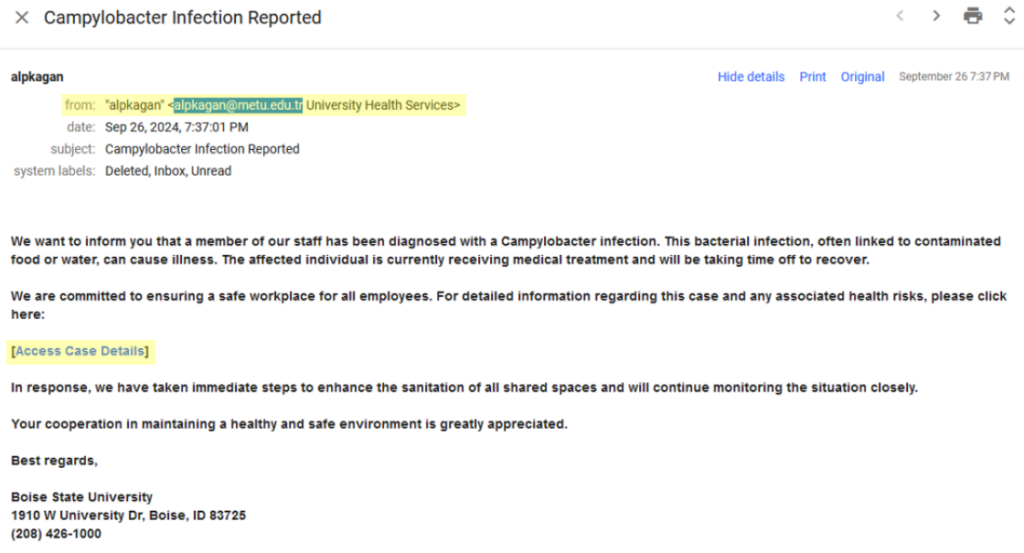
An email with the subject, “Campylobacter Infection Reported”* also caused several employees to respond by providing their Boise State credentials to hackers. We have seen many derivatives of this email message on campus, all of which use “Health Services” or “University Health Services” in the from: field.
*Variations on this subject line include “Monkeypox,” “Mpox,” and “COVID.”
Signs this was a phishing attempt
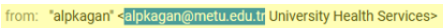
The email was sent from ‘alpkagan@metu.edu.tr’: The email is from ‘alpkagan@metu.edu.tr,’ clearly not a Boise State address. Always check the sender’s email closely, and be cautious of any non-university addresses.

Suspicious request: The email asks recipients to click a link that goes to an authentication page to view case details. Health-related emails rarely require login authentication, especially for viewing sensitive information. The curly braces surrounding the link text are red flag and should prompt caution.
Fake login page (again): The link directed employees to the same fake Boise State login page (along with the same fake Duo Security prompts) mentioned in the Workplace Safety Email section above.
How you can protect yourself
You are the best prevention against phishing attempts.
As phishing scams grow more sophisticated, your vigilance is the best line of defense. Here’s what you can do:
- Examine emails carefully: Before clicking any link, take a moment to scrutinize the email. Look for discrepancies like unusual sender addresses, department names, odd formatting, and requests that feel out of place.
- Emails on mobile devices require additional caution: It may be difficult to determine the actual account sender or other significant warning signs of phishing. We suggest waiting to take any action on an email that could be a phishing attempt until you can review the email on a desktop or laptop computer.
- Don’t fall for urgency: Phishing emails often create a sense of urgency to prompt quick actions without thinking. Be cautious of emails that insist you act immediately.
- Verify links before clicking: Hover over links to see where they actually lead. If the web address doesn’t look like a Boise State address, don’t click it.
- Consult the Help Desk: If you’re unsure about an email, don’t take a risk. Contact the Help Desk at (208) 426-4357 or email helpdesk@boisestate.edu to verify its legitimacy.
- Be careful with Duo prompts: Always treat Duo prompts that appear when you are not actively logging in as suspicious.
- Remember: Boise State will never ask for your username and password via email or any online form.
Report phishing
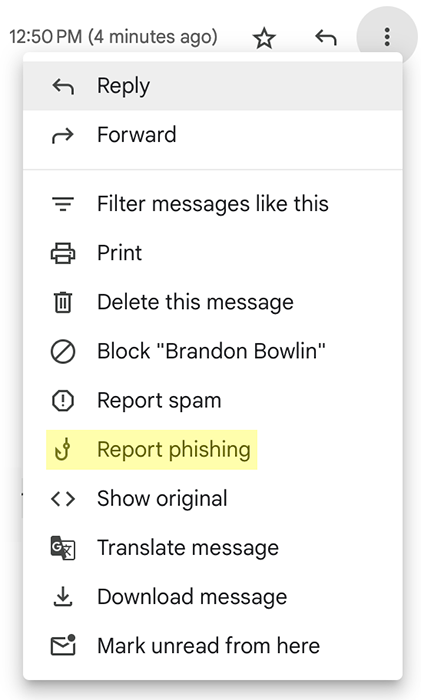
You may also report phishing emails within Gmail by selecting the three vertical dots at upper-right in the message and selecting Report phishing from the drop-down menu.
By staying alert and learning to recognize phishing tactics, you play a crucial role in keeping our university community safe.
Contact the Help Desk at (208) 426-4357 or email helpdesk@boisestate.edu for additional information.